Posts
Showing posts from March, 2020
Impact Of ISO 27001 Lead Auditor
- Get link
- X
- Other Apps

Information Security Management System ISO 27001 Standard is an Information Security Management System. The main objective of this standard is the organization shall establish, implement and maintain the information security system within the organization. Evaluate the information security Risk at each stage of operation and take the necessary action to reduce the information security Risk within the organization. In common business practice the ISO 27001 standard is also referred as ISMS standard. The summarized requirement details of ISO 27001 are given below: Context of The Organization The organization shall identify the internal and external issue related to information security , including the legal, regulatory and contractual requirements. Determining the scope of information security management system and establishing the information security management system. Leadership The top management of the organization demonstrates the leadership and ...
General Data Protection Regulation & Personal Data Protection | Training...
- Get link
- X
- Other Apps
Top 9 Challenges IT Leaders Will Face In 2020 Now
- Get link
- X
- Other Apps

Challenges IT Leaders With 2020 underway, digital transformation remains considerably attention for business leaders — but what about the processes getting used to hit those targets? According to Stephanie Over by at The Enterprise Project, DX preparation is ongoing, but full culture change is on the horizon for 2020. The gig economy It’s few secret that both the gig economy and telecommuting are exploding. Thereupon comes the difficulty of data and IP security. While the benefits of distributed teams include flexibility and quick-pivoting, the aforementioned Gartner report warns that “A growing remote workforce, in both a work-from-home and co-work-space model will unintentionally expose the organization to vulnerabilities in data privacy and therefore the security of tip .” Another gig economy concern? Finding the proper talent. Data privacy The specific requirements of the GDPR and...
10 Secrets You Will Never Know About Cyber Security And Its Important
- Get link
- X
- Other Apps

Know about Cyber Security Whether you’re a techie or not, there’s a good chance that your life is very reliant on the net and its wonders. Your social media accounts are likely humming, and you recognize your way round the IOT devices you employ . All of those devices connect you to the cyber world in a method or another. Here are 12 things to understand about cyber security . And once you are sharing such a lot of your data online daily, you may also care about your cyber security. If you’ve always thought cyber security are a few things only big companies got to care about change your mind, now. Cyber security is as critical on a private level, because it is on a company’s level. Besides, there’s hardly any job or profession, that’s not supported technology. With jobs or a career in mind , you need to understand what threatens your security online and what you’ll be able to do to stay your data secure. 1 You’re a target to hackers Don’t ever say...
EC-Council Certified Incident Handler | ECIHv2 Training with Certificati...
- Get link
- X
- Other Apps
EC-Council Certified Incident Handler | ECIHv2 Training with Certificati...
- Get link
- X
- Other Apps
Web Server Concept
- Get link
- X
- Other Apps
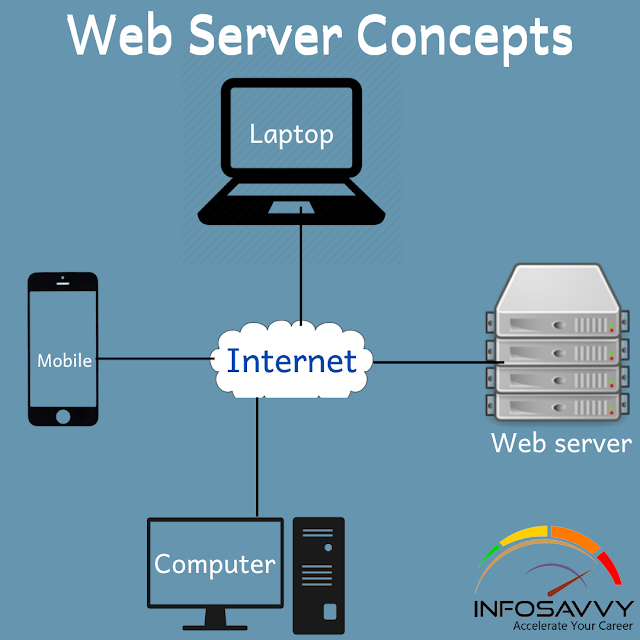
Concept Web server hacking, first you should understand web server concepts like what a internet server is, how it functions, and therefore the other elements associated with it. This section gives a quick overview of the online server and its architecture. it’ll &so explain common reasons or mistakes made that allow attackers to hack an internet server successfully. This section also describes the impact of attacks on the online server. Web Server Operations A Concept web server may be a computing system that stores, processes, and delivers sites to the global clients via HTTP protocol. generally , a client initiates the communication process through HTTP requests. When a client wants to access any resource like sites , photos, videos, and so on, then the client’s browser generates an HTTP request to the online server, depending on the request, the online server collects the requested information/content from the ...
PCI DSS Implementation Training and Certification | PCI DSS Implementati...
- Get link
- X
- Other Apps
ISO 27001 LA Training Courses | ISO 27001 Lead Auditor | Infosavvy
- Get link
- X
- Other Apps
CEHv10 Training and Certification | Certified Ethical Hacker | Infosavvy
- Get link
- X
- Other Apps
Sniffing Technique : DHCP Attacks
- Get link
- X
- Other Apps
This section discusses the DHCP attacks. A DHCP attack is an active sniffing technique used by the attackers to steal and manipulate sensitive data. This section describes how DHCP works, DHCP starvation attacks, tools used for starvation attacks, rogue server attacks, and the ways to defend against DHCP attacks. How DHCP Works Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that gives an IP address to an IP host. additionally to the IP address, the DHCP server also provides configuration-related information like the default gateway and subnet mask. When a DHCP client device boots up, it participates in traffic broadcasting. DHCP can assign IP configuration to hosts connecting to a network. The distribution of IP configuration to hosts simplifies the administrator's work to take care of IP networks. DHCP servers maintain TCP/IP configuration information during a database like valid TCP/IP configuration parameters, valid IP addresses, and durat...