Web Server Concept
Concept Web server hacking, first you should understand web server concepts like what a internet server is, how it functions, and therefore the other elements associated with it.
This section gives a quick overview of the online server and its architecture. it’ll &so explain common reasons or mistakes made that allow attackers to hack an internet server successfully. This section also describes the impact of attacks on the online server.
Web Server Operations
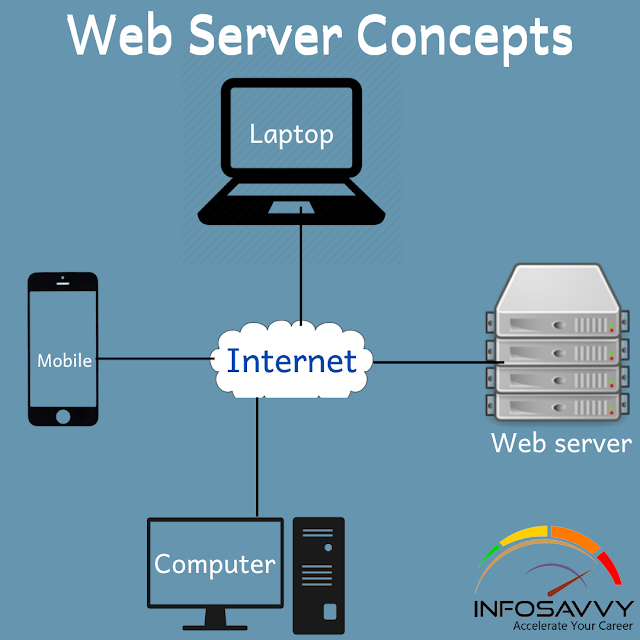
A Concept web server may be a computing system that stores, processes, and delivers sites to the global clients via HTTP protocol. generally , a client initiates the communication process through HTTP requests. When a client wants to access any resource like sites , photos, videos, and so on, then the client’s browser generates an HTTP request to the online server, depending on the request, the online server collects the requested information/content from the data storage or from the appliance servers and responds to the client’s request with an appropriate HTTP response. If an internet server cannot find the requested information, then it generates a mistake message.
Components of a Web Server
A web server consists of the following components: Document Root
Document root is one of the web server’s root file directories that stores critical HTivl files related to the web pages of a domain name that will serve in response to the requests.
- Server Root
It is the top-level root directory under the directory tree during which the server’s configuration and error, executable, and log files are stored. It consists of the code that implements the server. The server root, generally , consists of 4 files where one file is dedicated to the code that implements the server and other three are subdirectories, namely, -conf, -logs, and -cgi-bin used for configuration information, store logs, and executables, respectively.
- Virtual Document Tree
Virtual document tree provides storage on a different machine or a disk after the original disk is filled-up. It is case sensitive and can be used to provide object-level security.
- Virtual Hosting
It is a technique of hosting multiple domains or websites on the same server. This allows sharing of resources between various servers. It is employed in large-scale companies where the company resources are intended to be accessed and managed globally.
Following are the types of virtual hosting:
– Name-based hosting
– IP-based hosting
– Port-based hosting
- Web Proxy
A proxy server sits in between the web client and web server, Due to the placement of web proxies, all the requests from the clients will be passed on to the web server through the web proxies. They are used to prevent IP blocking and maintain anonymity.
Open-source Web Server Architecture
Concept Open-source web server architecture typically uses Linux, Apache, My SQL, and PHP (LAMP) as principal components.
Following are the functions of principal components in open source web server architecture:
• Linux is that the server’s OS that provides secure platform for the online server
• Apache is that the web server component that handles each HTTP request and response
• MySQL may be a relational database wont to store the online server’s content and configuration information
• PHP is that the application layer technology wont to generate dynamic web page
Following are the functions of principal components in open source web server architecture:
• Linux is that the server’s OS that provides secure platform for the online server
• Apache is that the web server component that handles each HTTP request and response
• MySQL may be a relational database wont to store the online server’s content and configuration information
• PHP is that the application layer technology wont to generate dynamic web page
IIS Web Server Architecture
Internet information Service (IIS) may be a web server application developed by Microsoft for Windows. IIS for Windows Server may be a flexible, secure, and easy-to-manage web server for hosting anything on the online . It supports HTTP, HTTPS, FTP, FTPS, SMTP, and NNTP.
It has several components, including a protocol listener like HTTP.sys and services like World Wide Web Publishing Service (WWW Service) and Windows Process Activation Service WAS). Each component functions in application and web server roles. These functions may include listening to requests, managing processes, reading configuration files, and so on.
It has several components, including a protocol listener like HTTP.sys and services like World Wide Web Publishing Service (WWW Service) and Windows Process Activation Service WAS). Each component functions in application and web server roles. These functions may include listening to requests, managing processes, reading configuration files, and so on.
Web Server Security Issue
A Concept web server may be a hardware/software application that hosts websites and makes them accessible over the web . an internet server, along side a browser, successfully implements client-server model architecture during which the online server plays the server part within the model and therefore the browser acts because the client. To host websites, an internet server actually stores various sites of the websites and delivers the particular website upon request. Each web server has a domain name and therefore the IP address related to that name . an internet server can host quite one website. Any computer can act as an internet server if it’s specific server software (a web server program) installed in it and is connected to the web .
Concept Web servers are chosen based on their capability to handle server-side programming, security
characteristics, publishing, program , and site-building tools. Apache, Microsoft IIS Nginx,
Google, and Tomcat are some of the most widely used concept web servers. An attacker usually targets vulnerability that exists within the software component and configuration errors to compromise web servers.
Organizations can defend most network level and OS-level attacks by using network security measures like firewalls, IDS, IPS, then on and by following security standards and guidelines. This forces attackers to turn their attention to perform web server and web application-level attacks as web server hosting web applications is accessible from anywhere over the internet.
Concept Web servers are chosen based on their capability to handle server-side programming, security
characteristics, publishing, program , and site-building tools. Apache, Microsoft IIS Nginx,
Google, and Tomcat are some of the most widely used concept web servers. An attacker usually targets vulnerability that exists within the software component and configuration errors to compromise web servers.
Organizations can defend most network level and OS-level attacks by using network security measures like firewalls, IDS, IPS, then on and by following security standards and guidelines. This forces attackers to turn their attention to perform web server and web application-level attacks as web server hosting web applications is accessible from anywhere over the internet.
------------------------------------------------------------------------------------------------------------
This Blog Article is posted by
Infosavvy, 2nd Floor, Sai Niketan, Chandavalkar Road Opp. Gora Gandhi Hotel, Above Jumbo King, beside Speakwell Institute, Borivali West, Mumbai, Maharashtra 400092



I really liked your Information. Keep up the good work. Software Security Training
ReplyDeleteWeb Server Concept >>>>> Download Now
ReplyDelete>>>>> Download Full
Web Server Concept >>>>> Download LINK
>>>>> Download Now
Web Server Concept >>>>> Download Full
>>>>> Download LINK Si